7.3. Securing the kernel
The secure Linux kernel patches from the Openwall Project are a great way to prevent attacks like Stack Buffer Overflows, and others. The Openwall patch is a collection of security-related features for the Linux kernel, all configurable via the new Security options configuration section that will be added to your new Linux kernel. This patch may change from version to version, and some may contain various other security fixes.
New features of patch version linux-2_2_14-ow2_tar.gz are:
Non-executable user stack area
Restricted links in /tmp
Restricted FIFOs in /tmp
Restricted /proc
Special handling of fd 0, 1, and 2
Enforce RLIMIT_NPROC on execve(2)
Destroy shared memory segments not in use
: When applying the linux-2_2_14-ow2 patch, a new Security options section will be added at the end of your kernel configuration. For more information and description of the different features available with this patch, see the README file that come with the source code of the patch.
Applying the patch
- First we copy the program archive to the /usr/src directory
- then we move to the /usr/src directory
- decompress the linux-2_2_14ow2_tar.gz archive
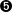
- We then move to the new uncompressed Linux patch, move the file linux-2.2.14-ow2.diff containing the patch to the /usr/src
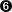
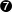
- return to /usr/src and patch our kernel with the file linux-2.2.14-ow2.diff
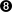
- Afterwards, we remove all files related to the patch.
: All security messages related to the linux-2.2.14-ow2 patch, like the non-executable stack part, should be logged to the log file /var/log/messages.
The step of patching your new kernel is completed. Now follow the rest of this installation to build the Linux kernel and reboot.