 10) Protection techniques
10) Protection techniques
 10) Protection techniques
10) Protection techniques
Protection techniques ease secure programming. If a program is large, uses some system classes, is designed by a team etc., this is important (and non-trivial) to impose some restrictions on access to non-local attributes.
Let us consider a data structure declared as a class. Some of its attributes should be accessible for the class users, the others should not. For instance, in class Bst (p.7) the attributes member and insert are to be accessible. On the other hand the attributes root, node and help should not be accessible, even for a meddlesome user. An improper use of them may jeopardize the data structure invariants.
To forbid the access to some class attributes the three following protection mechanisms are provided: close, hidden and taken.
The protection close defined in a class forbids remote access to the specified attributes. For example, consider the class declaration:
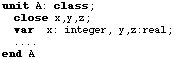
Remote access to the attributes x,y,z from outside of A is forbidden.
The protection hidden (with akin syntax) does not allow to use the specified attributes form outside of A neither by the remote access nor in the units prefixed by A. The only way to use a hidden attribute is to use it within the body of class A.
Protection taken defines these attributes derived from prefix, which the user wishes to use in the prefixed unit. Consider a unit B prefixed by a class A. In unit B one may specify the attributes of A which are used in B. This protects the user against an unconscious use of an attribute of class A in unit B (because of identifier conflict). When taken list does not occur, then by default, all non-hidden attributes of class A are accessible in unit B.


